It’s no shocking statement that telecommunication companies are a clear target for malicious adversaries. We only have to look at the TalkTalk data breach to see the devastating consequences a cyber attack can have on a company, and that’s not taking into account potential irreversible damage to brand reputation.
The data we store on our mobile devices and the information consumers freely give to telecom organisations is extremely valuable, so businesses taking care of this data must make security a top priority. Businesses need to change their mindsets as we are in an age where it is ‘when’ a cyber attack will hit and not ‘if’ it will at all.

An independent survey that Nlyte commissioned, showed that a breach or malicious attack is often the most compelling event to implement asset control across the entire technology stack, according to 26 per cent of IT teams’ respondents. It was also reported in CrowdStrike’s Global Security Survey that in 2019 that several China-based actor groups were linked to targeting telecom industry. With malicious Chinese adversaries banging on telecom organisations’ doors they must implement the correct solutions to ensure the networks they operate on are threat proof.
Considering these eye-boggling facts and horror stories, businesses must regain control over all assets and have complete visibility over all technology encountering with the complex ecosystems. Then they will be able to understand the lay of the land they are to defend.
Have you got your cyber hygiene in check?
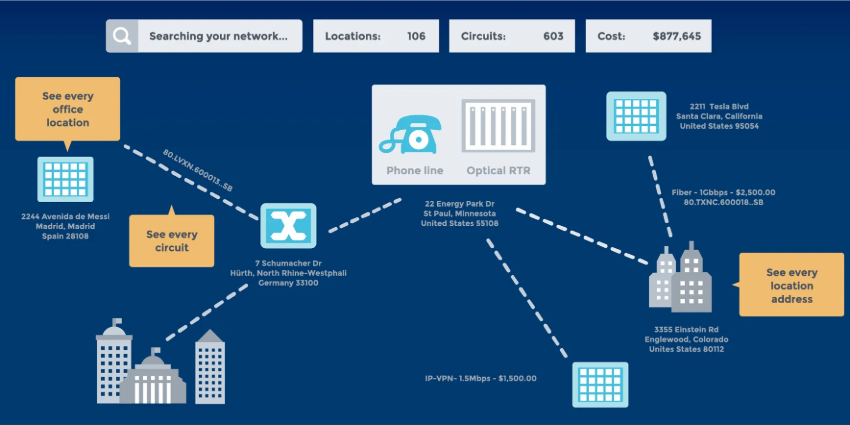
Telecom organisations have data and assets spread across the globe from the business’ own data centre to colocation and edge facilities. This can make managing all the assets extremely difficult, but this is not an excuse to have bad cyber hygiene.
Organisation are on the front line to a great variation and array of threats which can easily spiral into a business threatening cyber-attack when an opening is found. As IoT devices flicker on and off the network it is more than likely that devices installed or updated will not be fully compliant. The danger of having non-compliant technology interacting with the network is that it can open up a door for a bad actor to sneak through. Hackers do not follow one tactic to breach a system, they adapt and change to try and defeat security systems. IT teams must ensure that the correct security patches for firmware and software are applied and the right defences are likewise scrupulously kept up-to-date.
The regular maintenance of a datacentre is extremely time-consuming, especially if there is no automated solution in place, making an IT teams’ job very labour intensive.
Technology Asset Management (TAM) holds the key to taking back control and managing the huge ecosystem of telecoms companies’ networks. It can keep track of all assets across the entire network infrastructure and ensure that the correct patches are applied to ensure security defences are watertight.
Automated means ‘more secure’
When there is a security issue within a telecoms network is can be extremely difficult to pinpoint the exact problem due to the vast amount of data and assets being processed. This results in a complex and extremely inefficient process.
 TAM allows IT teams to have a holistic view over all the technology integrated with the network giving them a single source of truth to rely on. Once a TAM project is successfully implemented, IT managers will have complete visibility over a normally mind-boggling infrastructure, meaning that that managing costs, security, and compliance is fully understood and that insights can be delivered from across all assets, at pace.
TAM allows IT teams to have a holistic view over all the technology integrated with the network giving them a single source of truth to rely on. Once a TAM project is successfully implemented, IT managers will have complete visibility over a normally mind-boggling infrastructure, meaning that that managing costs, security, and compliance is fully understood and that insights can be delivered from across all assets, at pace.
TAM can do so much more than just give a clear view of a telecom’s infrastructure, it can ensure that the technology, software and hardware can be optimised. The solution searches across the whole network and seeks out any outdated or unused assets as well as anything at risk. All the outdated technology is therefore locked down and stops security threatening assets disrupting the network. TAM is constantly working in the background picking up the slack so IT teams can focus on prioritising more important innovation and customer care tasks to ensure the whole business stays healthy.
To successfully reduce cyber risks at telecommunication organisations, they must implement the correct solutions to ensure customers data is fully protected and the storing of assets are compliant with regulations. As hackers become more sophisticated so must the organisations holding the general public’s data. Cyber attacks will always be a challenge telecom companies come up against, but if they can outsmart and predict the bad actors business leaders can sleep easier with a well-managed risk profile.
Guest Blog by Rob Neave, CTO of Nlyte